Admin API security
Every mock API created has its own admin API (think of it as a standalone WireMock server per API), which is used for stubbing, verification, reset and a few other things. This has the same base URL as your mock API, with a base path of/__admin e.g. https://example.wiremockapi.cloud/__admin.
By default this is secured using the API token that can be found in https://app.wiremock.cloud/account/security.
The token can either be sent in an Authorization header e.g.
Authorization:Token 1kj3h98f7sihjfsf
or as a query parameter e.g.
https://example.wiremockapi.cloud/__admin/mappings?apiToken=1kj3h98f7sihjfsf.
It is recommended that you use the header approach where possible as this reduces the risk of the key appearing in log files an browser histories.
Disabling admin security
Admin API security can be disabled from the Settings page for the API: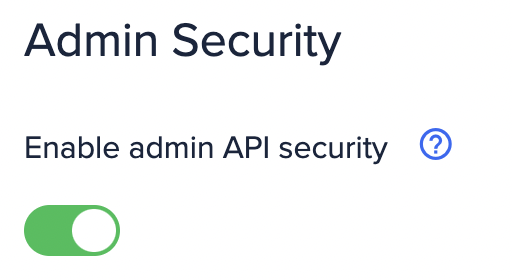
Admin API security will be disabled by default for APIs created prior to the security feature being released.
Mock API security
Mock APIs can optionally be configured to authenticate callers. At present this can be via HTTP Basic authentication (username + password) or an arbitrary header match, as well as OpenID Connect authentication for Enterprise plan users.HTTP Basic authentication
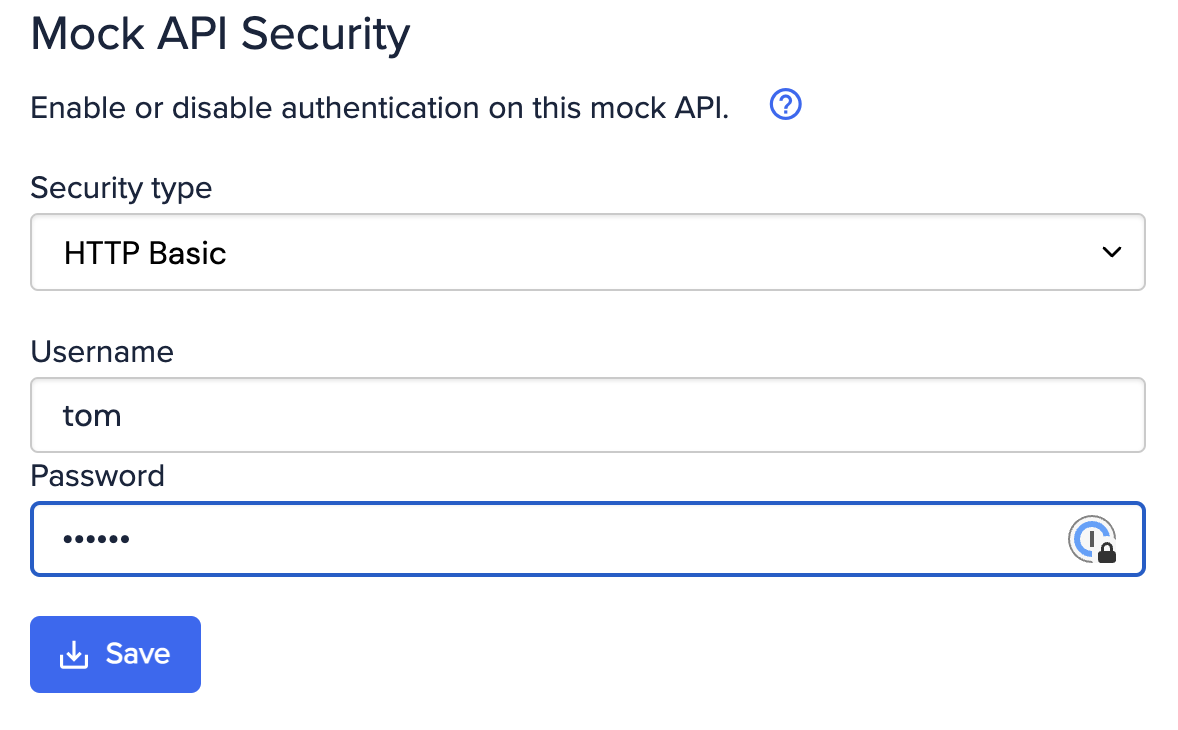
Authorization:Basic <base64 encoded username:password>.
Header match authentication
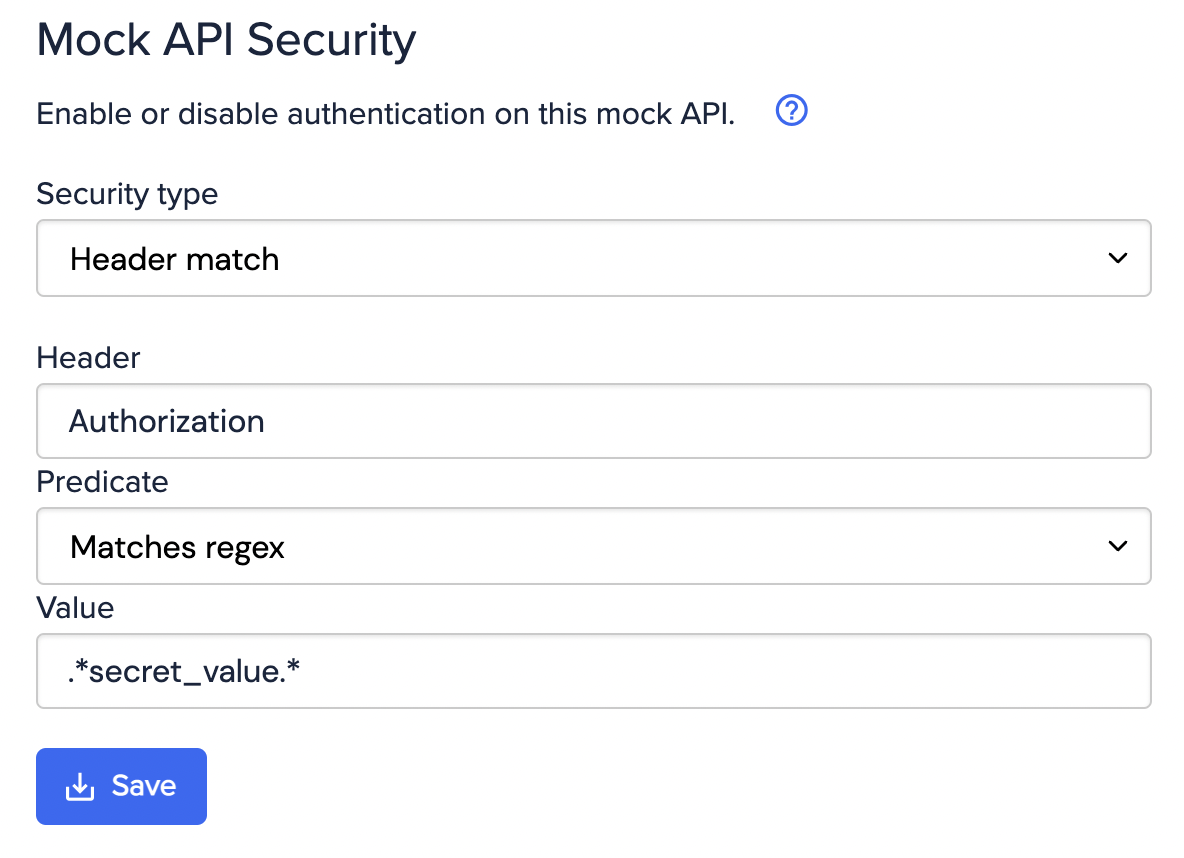
OpenID Connect authentication
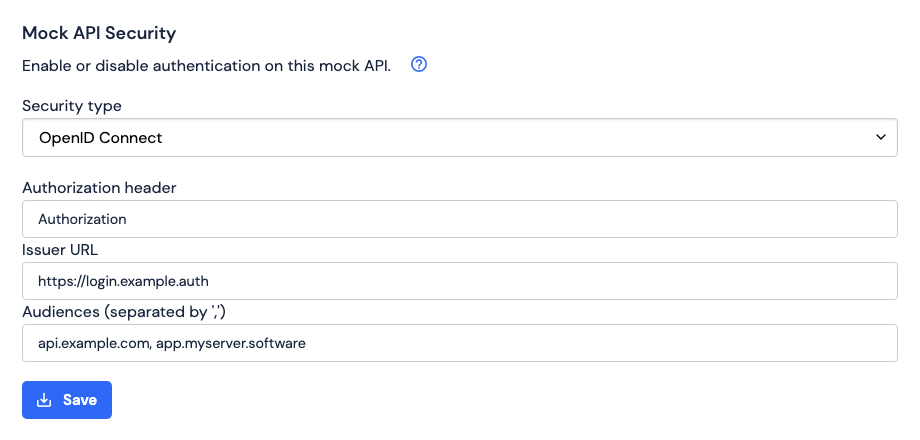
Authorization, but any valid HTTP header name is allowed).
The value of the Issuer URL field must be the base URL of the authorization server.
The authorization server is expected to be configured as per
the OpenID Connect specification.
Specifically /.well-known/openid-configuration contains the required configuration information, including the URL to
the JSON Web Key Set (JWKS) that contains the key(s) to verify the JWTs’ signatures.
The value of the Audiences field can optionally be a set of required audiences.
If this field’s value is non-empty, every JWT’s
aud claim must contain all of these audiences for the
JWT to be considered valid.