Usage
The audit event feature is only available to users on our Enterprise or Enterprise Trial plans and you will need to be an organisation administrator to create and manage audit event destinations. To create and manage your S3 bucket destination, navigate to the Organisation Page on your account. On this page you will see theAudit Events section.
Configure Your AWS Account
The first step in setting up your S3 audit event destination is to configure your AWS account to allow WireMock Cloud to save audit events to your bucket. You can do this in the following way:- Create the S3 bucket
<your-company-name>-wiremock-cloud-audit-events(you can use any bucket name if you have your own naming convention but be sure to update the bucket name in the examples below) - Create a policy called
wiremock-cloud-put-audit-eventswiths3:PutObjectonarn:aws:s3:::<your-company-name>-wiremock-cloud-audit-events/*
- Create an AWS account role for another AWS account
- Specify account id
499333472133. - Do NOT require external ID or MFA.
- Choose
wiremock-cloud-put-audit-eventsas the policy (the one you created above) - Name it
wiremock-cloud-put-audit-events - Set the trust policy as so:
- Specify account id
Configure Your WireMock Cloud Account
Now you have configured your AWS account with the new bucket and role, you can add those details to theAudit Events
section on the Organisations page:
- Enter the bucket name into the
Bucket namefield - Enter the full role arn into the
Role ARNfield
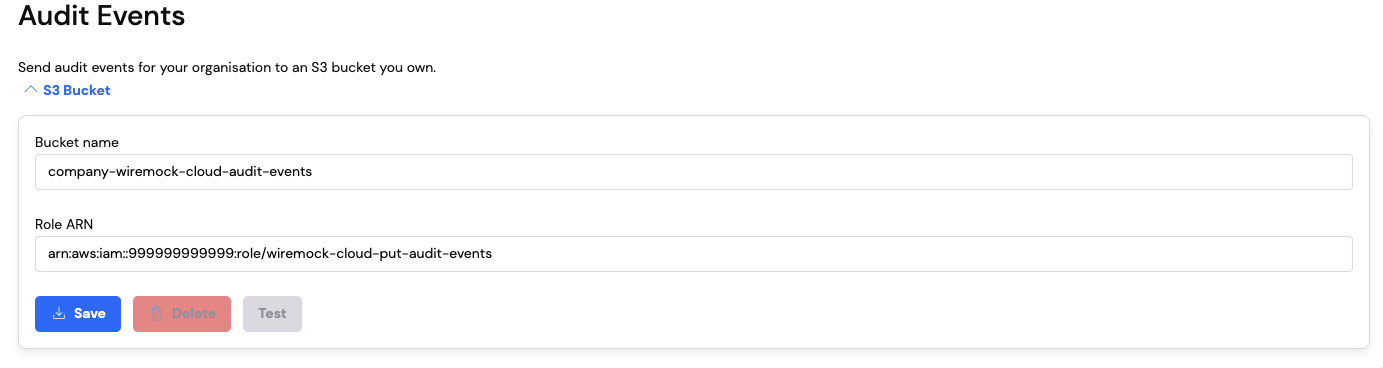
- Click on the
Savebutton to add the S3 audit destination to your organisation
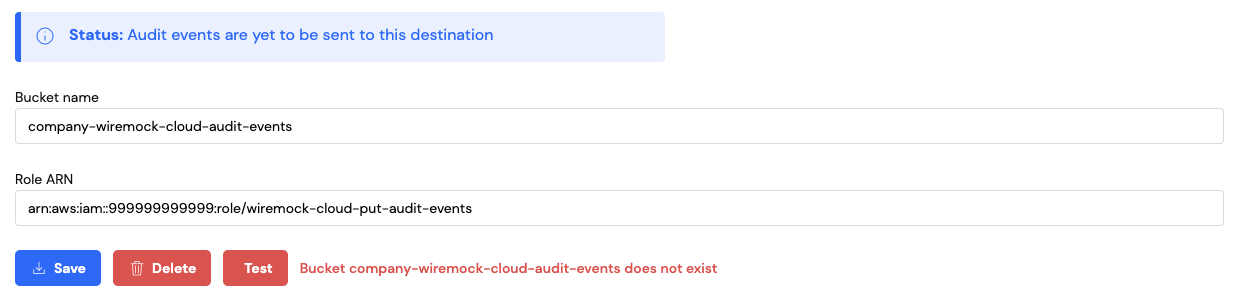
Status: Audit events are yet to be sent to this destination
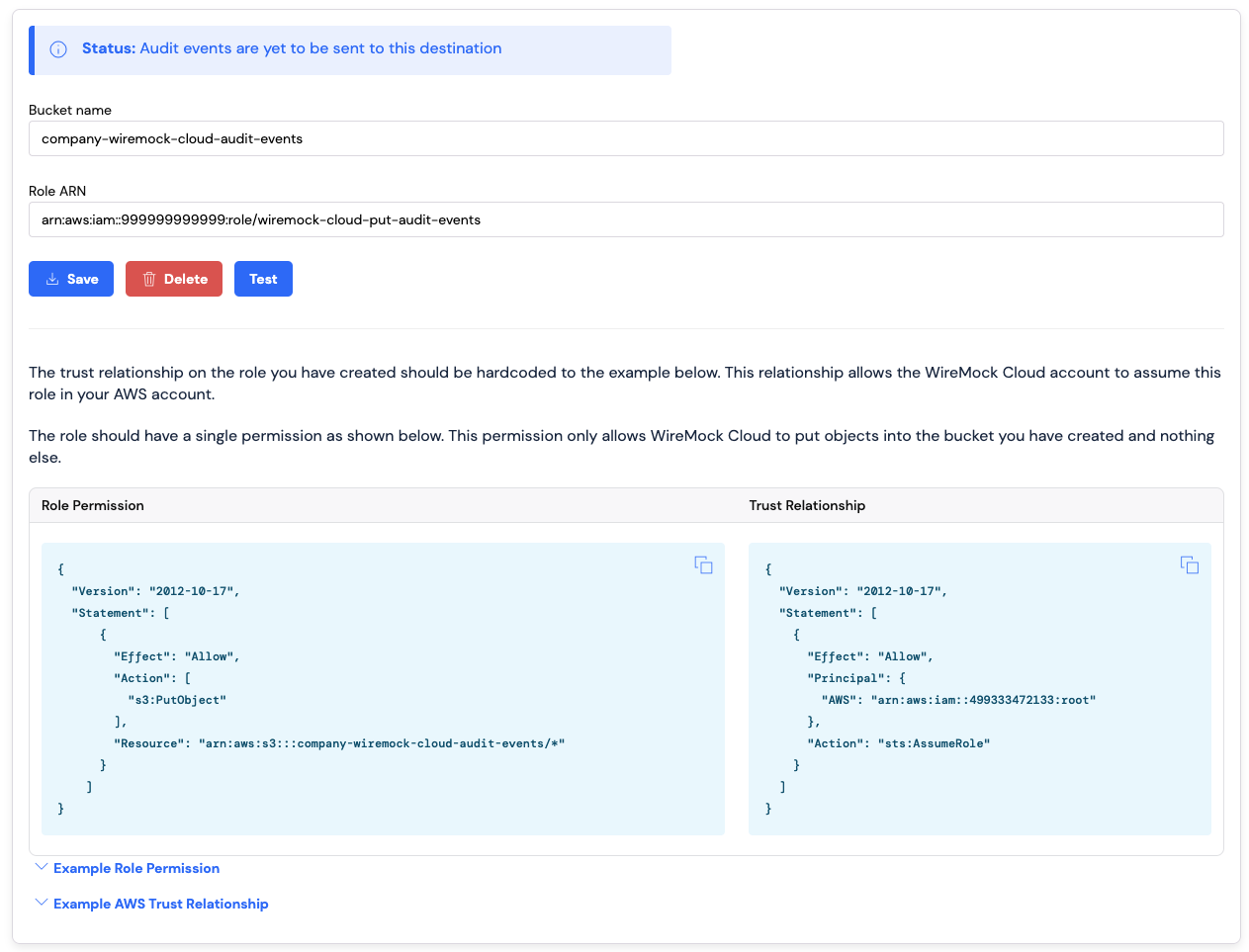
Testing Your S3 Audit Event Destination
Now you saved the S3 audit event destination you can test it to make sure everything works end to end. Clicking on theTest button will make WireMock Cloud attempt to post a test file to the bucket you created above. If all works
correctly the button will turn green and you should have a new file saved to your S3 bucket called test-wiremock-cloud-integration.txt.
This file will contain the date and time the test was performed.
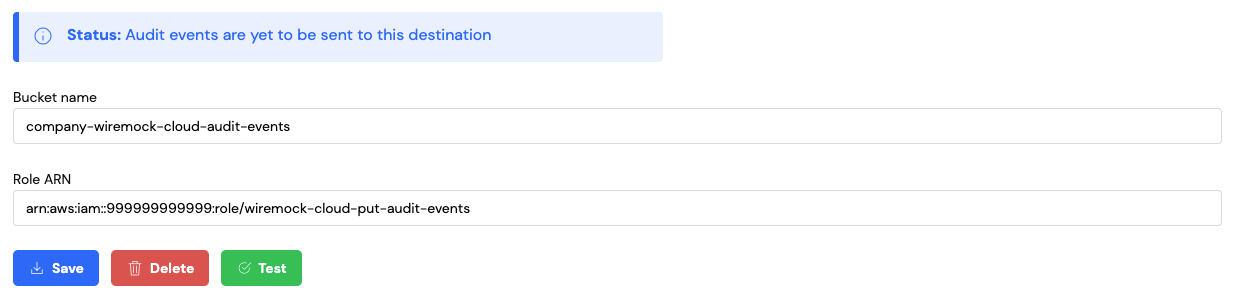
Deleting Your S3 Audit Event Destination
If you no longer require audit events to be sent to your S3 bucket you can delete the audit event destination from your organisation. This will stop audit events being set to your S3 bucket. To do this you can click on theDelete
button. This will display a confirmation dialog to allow you to confirm the deletion.
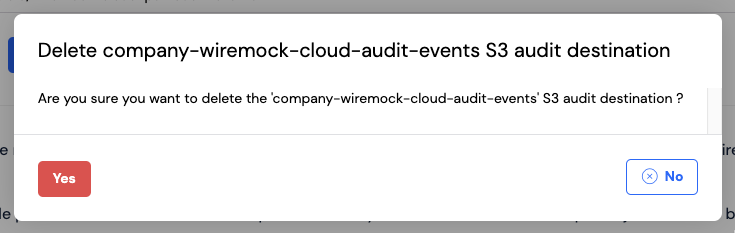
No will close the dialog and no action will be taken, clicking on Yes will delete your S3 audit event
destination and no more audit events will be sent.
Sending Audit Events To Your S3 Bucket
WireMock Cloud will send audit events to your S3 bucket in batches every 10 minutes. There is a lookback window of 7 days for audit events. This means if you are setting up an S3 audit event destination and have been a customer for a while, the first batch of audit events sent to your bucket will span back 7 days prior to the date you setup the destination. Once audit events are successfully being sent to your bucket you will see the status message update on the Organisation page: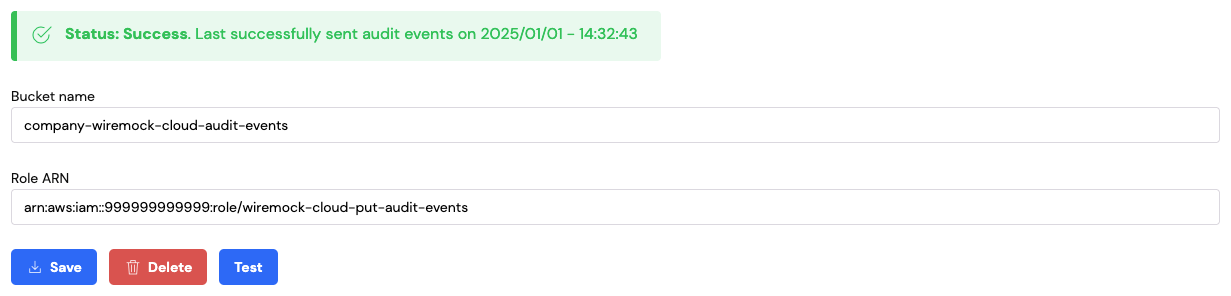
- Mock APIs
- Users
- Teams
- Organisations
- API Templates
- API Template Catalogues
- Data Sources
- Database Connections
- Keys
- Stub Mappings
- Mock API Settings
- Subscriptions
- Open API Git Integrations
- API Keys
- S3 Audit Destinations